CIDRAM (short for “Classless Inter-Domain Routing Access Manager”) is a web security tool that helps protect websites from malicious traffic. It uses a combination of IP blocking, HTTP header analysis, and other techniques to identify and block threats in real-time. CIDRAM is open-source software and can be easily integrated into various web applications, including WordPress, Drupal, and Joomla.
In this article, we will discuss the importance of CIDRAM in web security and its main features. We will also look at how CIDRAM works, how it can be installed and configured, and how it can be used to enhance the security of your web applications.
What is CIDRAM?
As the internet continues to grow and evolve, so do the threats that come with it. One of the most significant threats facing website owners and users alike is the risk of cyberattacks, which can result in data breaches, identity theft, and other forms of digital crime. To help protect against these threats, a variety of security tools and techniques have been developed, including Content-Intrusion Detection and Response Advanced Module (CIDRAM). By implementing CIDRAM on a website, site owners can enhance their security measures and reduce the risk of cyberattacks.
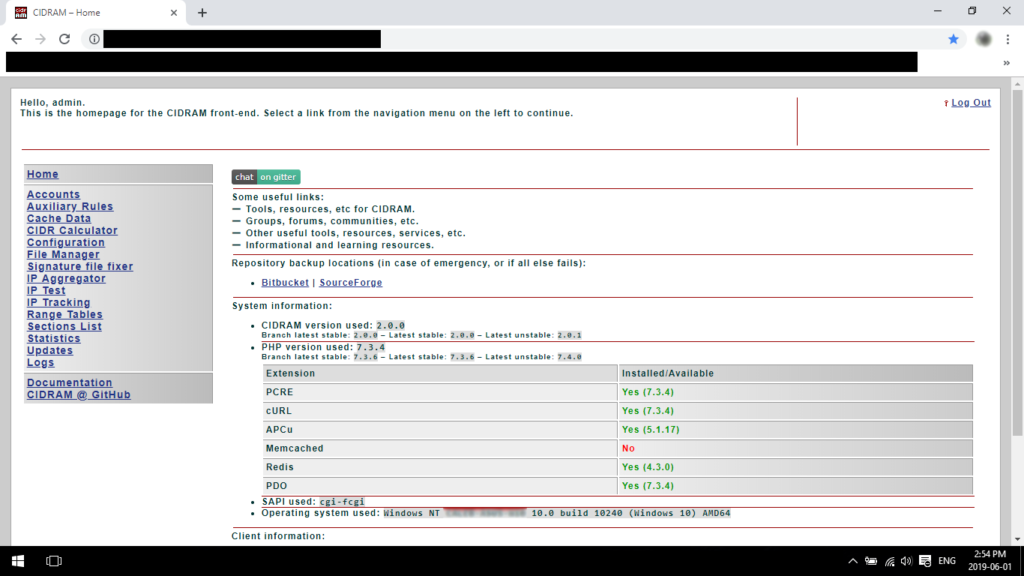
The tool works by analyzing incoming traffic and comparing it to a set of rules and filters, which are based on IP addresses, user agents, referrers, and other parameters.
CIDRAM’s main goal is to prevent various types of attacks, such as brute-force attempts, SQL injections, cross-site scripting, and others. By filtering out suspicious traffic, it helps to reduce the server load, improve the website’s performance, and enhance the overall security posture. Additionally, CIDRAM provides various customization options, allowing developers to tailor its settings to their specific needs and configurations.
The development of the project started in 2016 by Caleb Mazalevskis, who was looking for a way to effectively protect his websites from malicious visitors. It gained popularity over time, with more and more users adopting it for their own websites. The project has a strong community of contributors and users who help with its development and provide support to others. While there are other competitors in the web security space, CIDRAM’s unique features and ease of use have made it a popular choice among web developers.
How does CIDRAM work?
With a basic understanding of what CIDRAM is and why it’s important, let’s take a closer look at how it actually works. In this section, we’ll explore the key components of CIDRAM and how they work together to provide powerful protection against malicious traffic. From the initial request to the final decision on whether to allow or deny access, we’ll examine the steps involved in CIDRAM’s filtering process and the algorithms used to detect and block potentially harmful requests.
How CIDRAM blocks IP addresses
CIDRAM blocks IP addresses based on its IP database, which is regularly updated with the latest threat data. The database contains a list of IP addresses and ranges associated with malicious activity, such as spamming, phishing, and hacking attempts. When a request is made to a website protected by CIDRAM, the user’s IP address is compared to the entries in the database. If there is a match, the request is denied and the user is blocked from accessing the website.
CIDRAM uses a scoring system to determine the risk level of an IP address. Each entry in the database is assigned a score based on the severity of the threat it poses. When a request is made, CIDRAM calculates a score for the user’s IP address based on its history and the number of hits it has received. If the score exceeds a certain threshold, the user is blocked from accessing the website.
CIDRAM also uses a variety of other techniques to detect and block malicious activity. These include blacklisting of known bad IP addresses, whitelisting of known good IP addresses, and rate limiting to prevent brute force attacks. Overall, CIDRAM provides a comprehensive and effective solution for protecting websites from a wide range of security threats.
CIDRAM’s algorithms and filters
CIDRAM’s algorithms and filters are at the core of its functionality. The system employs various algorithms to determine whether or not an incoming IP address should be blocked. These algorithms include blacklist and whitelist checks, as well as pattern matching and user-defined rules. CIDRAM also uses a filtering system to determine which types of requests should be blocked or allowed. This filtering system can be customized to suit the specific needs of the website owner.
CIDRAM’s filters include country-based blocking, blocking of specific IP ranges, and detection of malicious requests based on patterns or signatures. Additionally, CIDRAM includes a real-time IP address lookup system to determine whether or not an IP address is associated with malicious activity. This lookup system includes integration with various databases and APIs to provide up-to-date information on IP addresses.
CIDRAM’s algorithms and filters work together to create a powerful and flexible system for blocking malicious IP addresses and requests. The system is designed to be customizable, allowing website owners to tailor CIDRAM’s functionality to meet their specific needs.
Comparison of CIDRAM with other security tools
CIDRAM is just one of many web security tools available today. Some of its competitors include ModSecurity, Fail2Ban, and NAXSI.
ModSecurity is an open-source web application firewall (WAF) that works as an Apache or Nginx module. It can monitor and analyze HTTP traffic in real-time, detect and block various types of web attacks, and log relevant information for further analysis. ModSecurity offers a wide range of security rules that can be customized and updated regularly to keep up with the latest threats.
Fail2Ban is another open-source tool that monitors log files and blocks IP addresses that have repeated failed login attempts or other suspicious behavior. It can be used for a variety of services, such as SSH, FTP, and Apache, and supports different ban actions, such as blocking IP addresses for a certain period of time or sending notification emails.
NAXSI is a WAF that uses a negative security model to block requests that match predefined rules. It can be used as a standalone WAF or as a module for Nginx. NAXSI is designed to be lightweight and easy to configure, and it offers a range of security rules that can be adjusted according to the specific needs of a website.
When it comes to comparing CIDRAM with these tools, it’s important to note that each one has its own strengths and weaknesses. For example, ModSecurity offers a wide range of security rules, but it can be complex to set up and maintain. Fail2Ban is easy to use and can be customized for different services, but it may not be effective against sophisticated attacks. NAXSI is lightweight and easy to configure, but it may require more advanced knowledge to use effectively.
CIDRAM, on the other hand, offers a lightweight and modular solution that is designed to be easy to use and highly customizable. It uses a range of algorithms and filters to block malicious requests and has a flexible configuration system that allows users to define their own custom rules. While CIDRAM may not offer the same range of features as some of its competitors, it provides a solid and reliable solution for web security that is well-suited for smaller websites and projects.
Features of CIDRAM
List of key features of CIDRAM
- IP Blocking: blocks IP addresses based on certain criteria, such as IP reputation, geographic location, known malicious IPs, etc.
- Log Analysis: analyzes server logs and detects malicious activity by using heuristics, pattern recognition, and other techniques.
- Whitelisting: allows you to whitelist specific IPs or ranges of IPs, so that they are not blocked by mistake.
- Custom Filters: provides a set of pre-configured filters, but you can also create your own custom filters based on your specific needs.
- Lightweight: CIDRAM is a lightweight and efficient tool, which means it won’t slow down your server or consume too many resources.
- Customizable: highly customizable, allowing you to fine-tune its settings and filters to meet your specific security needs.
- Integration: can be integrated with various web servers and content management systems, such as Apache, Nginx, WordPress, and more.
- Open Source: which means you can download, use, and modify it for free.
- User-Friendly: CIDRAM is designed to be user-friendly and easy to use, even for non-technical users.
Benefits of using CIDRAM for web security
- Robustness: CIDRAM is a powerful security tool that offers comprehensive protection against a wide range of web-based attacks such as DDoS, SQL injection, and XSS attacks.
- Efficiency: Unlike many other security tools that rely on blacklisting, CIDRAM uses efficient and lightweight algorithms to detect and block malicious traffic. This helps to minimize the impact on system resources and ensures maximum uptime for your website.
- Customization: With CIDRAM, you can customize the security rules to meet the specific needs of your website. This means you can create rules to block or allow traffic based on a range of criteria, including IP address, user agent, referrer, and more.
- Flexibility: CIDRAM can be easily integrated with your existing web application or CMS. It is compatible with a wide range of platforms including WordPress, Joomla, Drupal, and more.
- Open-source: CIDRAM is an open-source software, which means it is free to use and can be customized to suit your needs. The community of users and developers also ensures that the software is constantly updated with the latest security features and improvements.
- Scalability: CIDRAM is designed to be scalable and can handle large volumes of traffic without compromising on security. This makes it an ideal solution for websites that experience high traffic volumes.
- Ease of use: CIDRAM comes with a simple and user-friendly interface, which makes it easy to install, configure, and use. This means that even novice users can benefit from its advanced security features without the need for extensive technical expertise.
Installation and Configuration of CIDRAM
- Installation with Composer CIDRAM is registered with Packagist, so you can use Composer to install CIDRAM. Run the following command to install CIDRAM:
composer require cidram/cidram- Configuration After installing CIDRAM using Composer, you need to configure it to protect your website. To do this, create an “entrypoint” which consists of three things:
- Inclusion of the “loader.php” file at an appropriate point in your codebase or CMS.
- Instantiation of the CIDRAM core.
- Calling the “protect” method.
Here’s a simple example:
<?php
require_once '/path/to/the/vault/directory/loader.php';
(new \CIDRAM\CIDRAM\Core())->protect();If you’re using an Apache webserver and have access to php.ini, you can use the auto_prepend_file directive to prepend CIDRAM whenever any PHP request is made. In such a case, the most appropriate place to create your entrypoint would be in its own file, and you would then cite that file at the auto_prepend_file directive.
Example:
auto_prepend_file = "/path/to/your/entrypoint.php"Or this in the .htaccess file:
php_value auto_prepend_file "/path/to/your/entrypoint.php"In other cases, the most appropriate place to create your entrypoint would be at the earliest point possible within your codebase or CMS to always be loaded whenever someone accesses any page across your entire website. If your codebase utilizes a “bootstrap”, a good example would be at the very beginning of your “bootstrap” file. If your codebase has a central file responsible for connecting to your database, another good example would be at the very beginning of that central file.
Best Practices for Using CIDRAM
Tips for optimizing CIDRAM performance
- Use a caching mechanism: CIDRAM stores IP address information in a cache to speed up future lookups. You can configure CIDRAM to use a caching mechanism such as Memcached or Redis for improved performance.
- Minimize CIDRAM lookups: Although CIDRAM is optimized for speed, it still takes time to look up IP addresses. You can minimize the number of lookups by configuring CIDRAM to block IP addresses after a certain number of failed login attempts or other suspicious behavior.
- Use whitelists: Whitelists are lists of IP addresses that are trusted and should not be blocked. By using whitelists, CIDRAM can avoid unnecessary lookups and focus on blocking malicious IP addresses.
- Configure CIDRAM logging: CIDRAM can log blocked IP addresses and other information for debugging and analysis. However, logging can be resource-intensive and should be configured carefully to avoid performance issues.
- Use the latest version of CIDRAM: The CIDRAM project is constantly evolving, and new releases often include performance improvements and bug fixes. Make sure you are using the latest version of CIDRAM to get the best performance and security.
Keeping CIDRAM up-to-date and secure
- Regularly check for updates: It is important to keep up-to-date with the latest versions of CIDRAM to ensure that security vulnerabilities are addressed and new features are available. Check for updates on the official CIDRAM GitHub repository or website.
- Follow security advisories: Subscribe to security advisories from CIDRAM and other security organizations to stay informed about potential threats and vulnerabilities.
- Keep your server software up-to-date: Make sure your web server and PHP are updated to the latest stable versions. Outdated software can be vulnerable to security breaches.
- Use strong passwords: Use complex and unique passwords for all user accounts associated with CIDRAM, including the database.
- Limit access to CIDRAM files: Restrict access to CIDRAM files by setting proper file permissions and using secure authentication methods.
- Regularly backup CIDRAM data: Backing up CIDRAM data regularly can help you recover from data loss or corruption.
- Test updates before applying them: Test updates on a non-production environment before applying them to your live site to avoid unexpected issues or conflicts.
By following these best practices, you can help ensure that your CIDRAM installation remains secure and up-to-date.
Common Issues and Troubleshooting
Common issues
- False positives: CIDRAM may sometimes block legitimate traffic due to its filters and algorithms. To resolve this, users can adjust the filter settings to reduce false positives, or add exceptions for specific IP addresses or user agents.
- Compatibility issues: CIDRAM may not be compatible with certain web servers, PHP versions, or other software. To resolve this, users should ensure that they are using the latest version of CIDRAM and that their server environment meets the minimum requirements.
- Installation errors: Users may encounter errors during the installation or configuration process. To resolve this, users should carefully follow the installation guide and ensure that all dependencies are properly installed.
- Performance issues: In some cases, CIDRAM may slow down the server or consume excessive resources. To resolve this, users can optimize CIDRAM settings or upgrade their server hardware.
- Security vulnerabilities: Like any software, CIDRAM may have security vulnerabilities that could be exploited by attackers. To minimize the risk of these vulnerabilities, users should keep CIDRAM up-to-date with the latest security patches and follow best practices for server security.
Troubleshooting
- Check your CIDRAM logs: CIDRAM logs any blocked IPs and other relevant information. Check your logs to see if there are any patterns or recurring issues that may point to the source of the problem.
- Verify your configuration settings: Double-check that your CIDRAM configuration settings are correct and up-to-date. Pay close attention to any changes you may have made recently that could have caused issues.
- Check for conflicts with other security plugins or settings: CIDRAM may conflict with other security plugins or settings on your server. Check your server settings and any other security plugins you have installed to make sure there are no conflicts.
- Review your whitelist and blacklist settings: If you’re experiencing issues with CIDRAM blocking legitimate traffic or failing to block malicious traffic, review your whitelist and blacklist settings. Make sure they’re up-to-date and accurate.
- Upgrade to the latest version: If you’re running an older version of CIDRAM, consider upgrading to the latest version. This can help resolve any known issues and improve overall performance.
- Seek support from the CIDRAM community: If you’re still experiencing issues, reach out to the CIDRAM community for support. There may be others who have experienced similar issues and can offer guidance and solutions.
Conclusion
The security of a website is paramount, and with the rise of cyber threats, website owners need to take proactive measures to safeguard their online presence. One such tool that can help is CIDRAM, a powerful PHP-based security tool that offers a range of features to protect your website from malicious attacks. In this article, we’ve explored the key benefits of using CIDRAM, its various features, and how to install and optimize it for performance. We’ve also discussed common issues and troubleshooting tips for resolving problems with CIDRAM.
As a website owner, it’s crucial to prioritize web security, and CIDRAM provides a comprehensive solution that can help you achieve that. By using CIDRAM, you can have peace of mind knowing that your website is protected against a range of threats, including hacking attempts, spam, and DDoS attacks.
In conclusion, we encourage website owners to consider using CIDRAM as part of their web security strategy. It’s a powerful and effective tool that can help you protect your website and your users from online threats. Take the time to install and configure CIDRAM, and you’ll be one step closer to a more secure and resilient website.



























Hi author i think this cidram info is somewhat wrong or is out dated for starters their is no cidram-master folder found within the cidram zip file that makes everything else seem misleading in this guide. Just a heads up!
Thank you Jarad, yes you are correct. An old revision of the article have been published by mistake.