The PHP Git server was hacked yesterday, two malicious commits were pushed to the php-src repository from the names of Rasmus Lerdorf, the creator of PHP, and Nikita Popov pointed Nikita – the real one – in the PHP internals mailing list. The issue seems to be related to the official git.php.net server which seems to be compromised with a zero day bug but without any further detail until writing this article and the workflow to Git commit changed !
Contributions to the PHP source code moved then to Github officially, and developers need to be part of the PHP organisation on github to be able to contribute, in addition to enabling two factors authentication.
In the discussion many requested that commits should be signed, or at least in the main php-src repository as suggested Rasmus. It can remain optional for docs and other repositories until people are more comfortable with it.
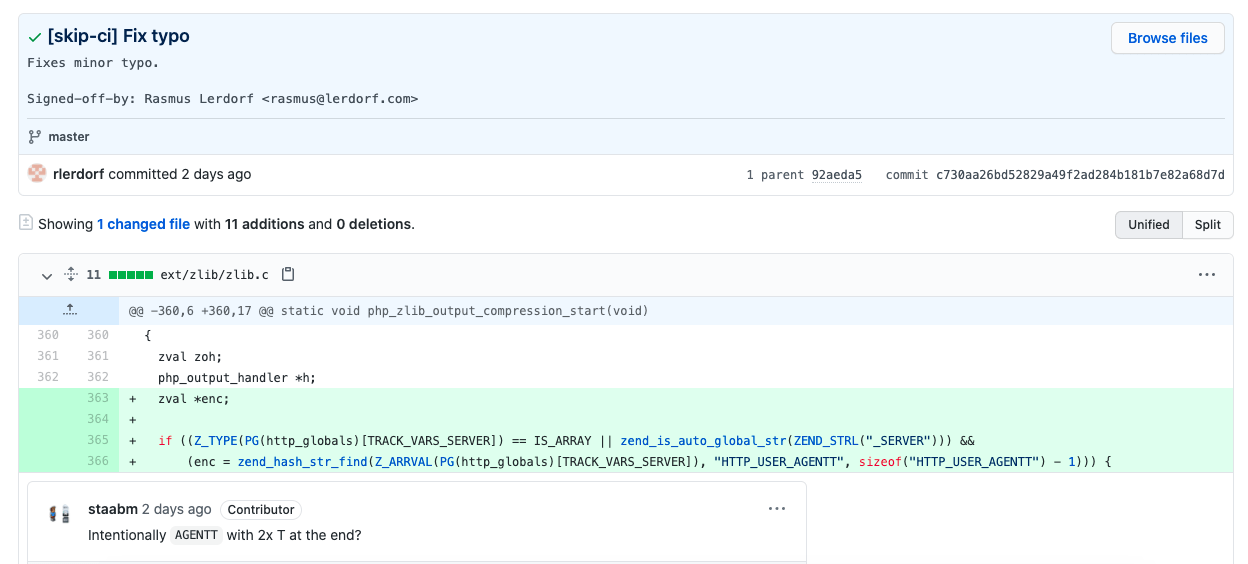
PHP Git server exploit origin
Could the issue be due to the git.php.net software used or its configuration. The server is actually running Gitweb, a a Git web interface written in Perl and can be used as a CGI script, or as a mod_perl legacy script. Gitweb was last updated on December 2020.
Many others pointed immediately to Zerodium, the leading exploits acquisition platform, which could be the reason behind since the user agent have the mention “sold to zerodium, mid 2017”. “The magic string searched for in the fake user agent, is a zero-day acquisition platform, in case anyone else is wondering”, pointed someone in a comment.
The CEO of Zerodium, posted a very strange tweet to decline any responsibility of the company. He added that the hacker who found the bug wanted to sell it to many entities, but none wanted to buy this useless crap !
The issue is not dangerous at all, and PHP source code is safe, however the PHP team are investigating the issue to find out the origin behind the exploit and if other servers or services are not also concerned.
Read the changes to Git commit workflow https://news-web.php.net/php.internals/113838